It’s the staple of all hacker and government-conspiracy fiction, not to mention quite a number of horror films: You’re being watched through your hacked computer or phone or through a hijacked surveillance camera feed. And, unfortunately, this is well-reasoned paranoia in the real world, because to an operating system, a camera is just another file that can be read and relayed.
Earlier this year, in response to the news and to reader queries, I went into detail with a few ways you could disable microphone input in software and hardware on a Mac. Video is surprisingly (or not so surprisingly) easier to block: You can simply put a piece of tape over a lens.
Security guru Christopher Soghoian, principal technologist at the ACLU, told an interviewer in August, “the best bang-for-buck when it comes to privacy…is putting a sticker or a Band-Aid over your webcam on your laptop.” That’s what Mark Zuckerberg did, and he also covered his mic—which, as I noted in the previous article, doesn’t help nearly as much as audio will still bleed through.
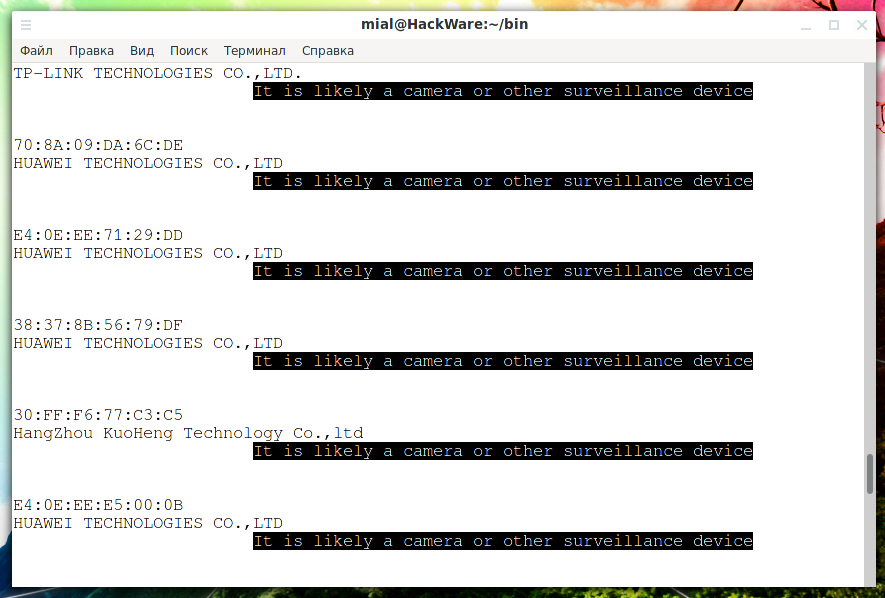
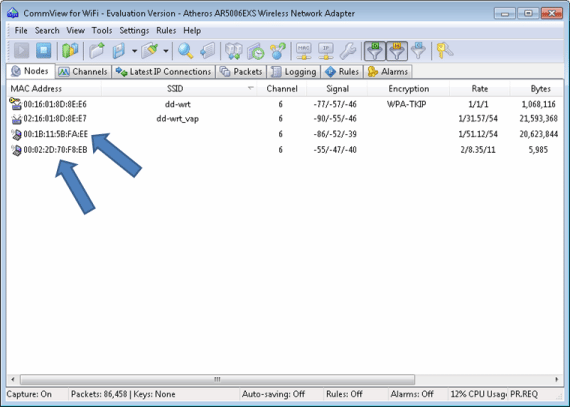
Download Technitium MAC Address Changer To manually change your MAC address in Windows 7 without using a third party software, go to Control Panel System Device Manager. Expand Network Adapters and double click on the network card that you want to change the MAC address. Go to Advanced tab and look for Network Address in the Property box. UPDATE: The MacMakeup website is down. You can download now download it from this link:video wil. A binary on the device called camregister was identified which contains the routine for obtaining the AES key for the device. This is handled on the initial camera setup over an SSL connection to the Hubble server. It sends an HTTP POST request with the MAC address, firmware version, UDID and a few other details. You can possibly find the MAC address of the IP camera if you know the device’s brand since the first 6-digits of a MAC address identify the manufacturer (You can also try.
Audio and video tapping don’t lend themselves per se to mass surveillance, despite the NSA reportedly recording enormous amounts of phone calls and video sessions and using software to find words and people of interest. Even its alleged efforts represent a fraction of all conversations, much less when you’re not actively engaged in an online A/V conversation with someone.
Soghoian explained in the above interview the likelihood of you being spied upon individually, which is worth a glance. Most people are unlikely targets, but any activist, any member of a group that finds itself in the minority, and anyone who someone else might feasibly have a grudge against could find themselves in the crosshairs of audio- and video-tapping malware or products.
Students and workers with equipment provided to them could also be monitored without their knowledge. The best-known incident, but absolutely not the only case, is when a school near Philadelphia revealed to a student they were watching him at home on a school-owned computer. The school district later settled for over $600,000.
So what you can do besides tape? Some new and existing software for macOS can help.
Scotch that recording
There’s a bit of chicken-and-egg problem with software tools that monitor, report on, and block access to microphones and cameras: they’re susceptible to malware, too. Software designed to hijack your A/V would likely be savvy enough to check whether kernel extensions or other software is also monitoring devices, and would try to disable or mislead them.
But the more widely spread malware is—that is, the less targeted for a very high-value individual or group—the less sophisticated it is, and the more likely it will give itself away.
I wrote about Micro Snitch ($4) in my column on microphones, and it alerts you when built-in and some third-party video cameras activate as well.
Security researcher Patrick Wardle has a passel of free apps designed to help you protect your privacy and system integrity, and his OverSight will monitor not just for usage, but “piggybacking.” This is a technique seen in malware that can tap into a stream being used for FaceTime, Skype, or local recording, so the camera, mic, or both are already active when the surveillance starts. OverSight will pop up an Allow/Block warning with details about what triggered it.
And a free version CameraGuard alerts you to use of your camera. A paid version ($30) adds microphone blocking, and its maker says it uses heuristics to identify likely unwanted audio and video uses.
It’s hard to recommend one above another, except for cost, because until malware strikes (or you intentionally install a known example to test on an unpatched system), it’s impossible to predict whether one will perform better than another.
But whichever you pick, pairing it with new software like Little Flocker and Wardle’s BlockBlock, which I wrote about recently, could help prevent software from running that tries to disable monitoring software or hijack active streams.
But what about an iPhone or iPad?
It’s much more complicated in iOS, because you don’t have access to the operating system’s innards and iPhones are more fragile. While iOS has a strong security track record in terms of exploits that have made it into the wild, plenty of severe flaws have been found and patched, and may have been used to target individuals. Recently, I wrote about the three-exploit package deployed against a human-rights activist’s iPhone in the United Arab Emirates, which—had it been successful—would have allowed remote audio and video interception on demand by the attackers.
You can simply put a black opaque sticker over the front-facing camera, or get a case that obscures both the front and back cameras.
It’s hard to argue that Apple could do more with iOS, because the locked-down nature of the system prevents the casual installation of third-party software that might commit unwanted acts and more serious attempts to quietly subvert your privacy. Any software that manage to hijack your mic or camera on an iOS device is the kind of thing that won’t go undiscovered in the wild for long, given how many researchers are watching for just this kind of attack.
Camera Mac Address Hacked
The last thread I saw on this ended in 2016.
I received what can only be described as a threatening email claiming a virus had been implanted and my camera had been hacked. The claim made was pretty weird, the language was non-native english (and not related to being from Belgium as the writer claimed; the email address country code was Hungary, surely nothing valid about any of it), and no mention was made of what my OS was, or anything specific to the machine or device of mine said to have been hacked.
Camera Mac Address Hack Tool
Of course **** sites were mentioned, they claimed to have accessed my address book, etc, and bitcoin was demanded. Their threat was to send a video out to my address book contents.

It most resembled what I have heard about ransomware emails. Surely I could have done something in front of my camera that would be embarrassing at some point or points, who can be sure, especially with the advent of sw methodology to edit faces onto other bodies, etc.
One odd thing was that the email address used to reach me is not one I use many places. We have our own domain and make up unique addresses for leaving at sites, etc.
Does the light come on with any activation of apple/mac cameras, or can that be circumvented?

Camera Mac Address Hack Free

Camera Mac Address Hack Download
Has anyone heard of an iPad, iPhone or Macbook camera hack, recently? If it is something possible on any Apple devices then I'll have to use tape on my camera when orgies are going on, or I'll have to cut back.
Posted on Mar 13, 2018 12:53 AM