hcxtools Description
- Kali Wifite Handshake Location
- Kali Wifite Handshake Location List
- Kali Wifite Handshake Location Map
- Kali Wifite
- Kali Wifite Handshake Location Code
Small set of tools convert packets from captures (h = hash, c = capture, convert and calculate candidates, x = different hashtypes) for the use with latest hashcat or John the Ripper. The tools are 100% compatible to hashcat and John the Ripper and recommended by hashcat. This branch is pretty closely synced to hashcat git branch (that means: latest hcxtools matching on latest hashcat beta) and John the Ripper git branch ('bleeding-jumbo').
Pyrit allows you to create databases of pre-computed WPA/WPA2-PSK PMKs. By using Multi-Core CPUs and ATI-Stream,Nvidia CUDA, and OpenCL, it is a powerful attack against one of the world's most used security-protocols. CudaHashcat or oclHashcat or Hashcat on Kali Linux got built-in capabilities to attack and decrypt or crack WPA WPA2 handshake.cap files. Only constraint is, you need to convert a.cap file to a.hccap file format. This is rather easy. Important Note: Many users try to capture with network cards that are not supported. To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Aircrack is one of the most popular tools for WEP/WPA/WPA2 cracking.
Support for hashcat hash-modes: 2500, 2501, 4800, 5500, 12000, 16100, 16800, 16801
Support for John the Ripper hash-modes: WPAPSK-PMK, PBKDF2-HMAC-SHA1, chap, netntlm, tacacs-plus
Homepage: https://github.com/ZerBea/hcxtools
Author: ZerBea
License: MIT
hcxtools Help
hcxtools is a common name of a set of tools, each executes only one specific function, and each has option set.
hcxpcaptool Help
hcxpcaptool shows info of pcap/pcapng file and convert it to other hashformats accepted by hashcat and John the Ripper.
usage:
options:
bitmask for message pair field:
- 0: MP info (https://hashcat.net/wiki/doku.php?id=hccapx)
- 1: MP info (https://hashcat.net/wiki/doku.php?id=hccapx)
- 2: MP info (https://hashcat.net/wiki/doku.php?id=hccapx)
- 3: x (unused)
- 4: ap-less attack (set to 1) - no nonce-error-corrections neccessary
- 5: LE router detected (set to 1) - nonce-error-corrections only for LE neccessary
- 6: BE router detected (set to 1) - nonce-error-corrections only for BE neccessary
- 7: not replaycount checked (set to 1) - replaycount not checked, nonce-error-corrections definitely neccessary
Do not use hcxpcaptool in combination with third party cap/pcap/pcapng cleaning tools!
hcxpsktool Help
hcxpsktool calculates candidates for hashcat based on commandline input, hccapx file and/or 16800 hash file (experimental).
usage:
options:
hcxhashcattool Help
hcxhashcattool calculate PMKs from hashcat -m 2500 potfile.
usage:
options:
wlanhcx2cap Help
wlanhcx2cap converts hccapx to cap.
usage:
options:
wlanhc2hcx Help
wlanhc2hcx converts hccap to hccapx.
usage:
options:
wlanwkp2hcx Help
wlanwkp2hcx converts wpk (ELMCOMSOFT EWSA projectfile) to hccapx.
usage:
options:
wlanhcx2essid Help
wlanhcx2essid merges hccapx containing the same ESSID.
usage:
options:
wlanhcx2ssid Help
wlanhcx2ssid strips BSSID, ESSID, OUI.
usage:
options:
wlanhcxinfo Help
wlanhcxinfo shows detailed info from contents of hccapxfile.
usage.:
options:

wlanhcxmnc Help
wlanhcxmnc help to calculate hashcat's nonce-error-corrections value on byte number xx of an anonce.
usage:
options:
wlanhashhcx Help
wlanhashhcx generate hashlist from hccapx hashfile (md5_64 hash:mac_ap:mac_sta:essid).
usage:
Kali Wifite Handshake Location
options:
wlanhcxcat Help
wlanhcxcat is a simple password recovery tool for WPA/WPA2/WPA2 SHA256 AES-128-CMAC (hash-modes 2500, 2501).
usage:
options:
input option matrix
wlanpmk2hcx Help
wlanpmk2hcx converts plainmasterkey and ESSID for use with hashcat hash-mode 12000 or john PBKDF2-HMAC-SHA1.
usage:
options:
wlanjohn2hcx Help
wlanjohn2hcx converts john wpapsk hashfiles for use with hashcat hash-modes 2500, 2501.
usage:
options:
wlancow2hcxpmk Help
wlancow2hcxpmk converts pre-computed cowpatty hashfiles for use with hashcat hash-mode 2501.
usage:
options:
Kali Wifite Handshake Location List
wlanhcx2john Help
wlanhcx2john converts hccapx to format expected by John the Ripper.
usage:
options:
wlanhcx2psk Help
wlanhcx2psk calculates candidates for hashcat based on the hccapx file (deprecated: will be replaced by hcxpsktool, soon).
usage:
options:
wlancap2wpasec Help
wlancap2wpasec uploads multiple caps to https://wpa-sec.stanev.org.
usage:
options:
Kali Wifite Handshake Location Map
whoismac Help
whoismac shows vendor information and/or download oui reference list.
usage:
options:
hcxtools Usage Example
Show detailed description of hashcat hashfile (NPAAE.hccapx):
Example output:
Show the hash list (format md5_64 hash:mac_ap:mac_sta:essid) of a file (NPAAE.hccapx):
Example output:
Read the file test.pcapng and create the test.16800 file of the PMKID hash for hacking into hashcat with hash mode -m 16800 (-z test.16800):
Example output:
How to install hcxtools
Installation on Kali Linux
Installation on BlackArch
Installation on Debian, Linux Mint, Ubuntu and their derivatives
Screenshots
Tutorials
Related tools
- WiFite (51.2%)
- mdk3 (51.2%)
- Aircrack-ng (Suite of Tools) (51.2%)
- Aircrack-ng (Tool) (51.2%)
- infernal-twin (51.2%)
- wifiphisher (RANDOM - 51.2%)
Recommended for you:
WiFite Description
To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Wifite aims to be the 'set it and forget it' wireless auditing tool.
Features
- sorts targets by signal strength (in dB); cracks closest access points first
- automatically de-authenticates clients of hidden networks to reveal SSIDs
- numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- customizable settings (timeouts, packets/sec, etc)
- 'anonymous' feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- all captured WPA handshakes are backed up to wifite.py's current directory
- smart WPA de-authentication; cycles between all clients and broadcast deauths
- stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- displays session summary at exit; shows any cracked keys
- all passwords saved to cracked.txt
- built-in updater: ./wifite.py -upgrade
Homepage: https://github.com/derv82/wifite2
Author: derv merkler
License: GPLv2
WiFite Help
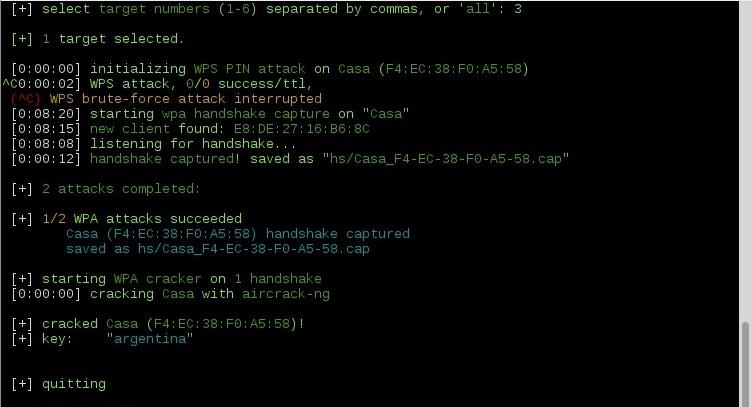
WiFite Usage Example
Attack access points with over 50 dB of power (-pow 50) using the WPS attack (-wps):
How to install WiFite
The program is pre-installed on Kali Linux.
Installation on Linux (Debian, Mint, Ubuntu)
Required Programs
Please see the installation guide on the wiki for help installing any of the tools below.
- Python 2.7.x. Wifite is a Python script and requires Python to run.
- aircrack-ng suite. This is absolutely required. The specific programs used in the suite are:
airodump-ng
packetforge-ng
Standard linux programs.
- iwconfig, ifconfig, which, iw
Suggested Programs
- reaver, a Wifi-Protected Setup (WPS) attack tool. Reaver includes a scanner 'walsh' (or 'wash') for detecting WPS-enabled access points. Wifite uses Reaver to scan for and attack WPS-enabled routers.
- pyrit, a GPU cracker for WPA PSK keys. Wifite uses pyrit (if found) to detect handshakes. In the future, Wifite may include an option to crack WPA handshakes via pyrit.
- tshark. Comes bundled with Wireshark, packet sniffing software.
- cowpatty, a WPA PSK key cracker. Wifite uses cowpatty (if found) to detect handshakes.
WiFite Screenshots
WiFite Tutorials
Kali Wifite
Related tools
- Penetrator-WPS (76.8%)
- Router Scan (75%)
- OneShot (74.2%)
- Fern Wifi Cracker (73.2%)
- airgeddon (70.6%)
- Crunch (RANDOM - 2%)